I am new to the MikroTik world and am a novice network engineer at best. I appreciate any advice in advance.
My setup:
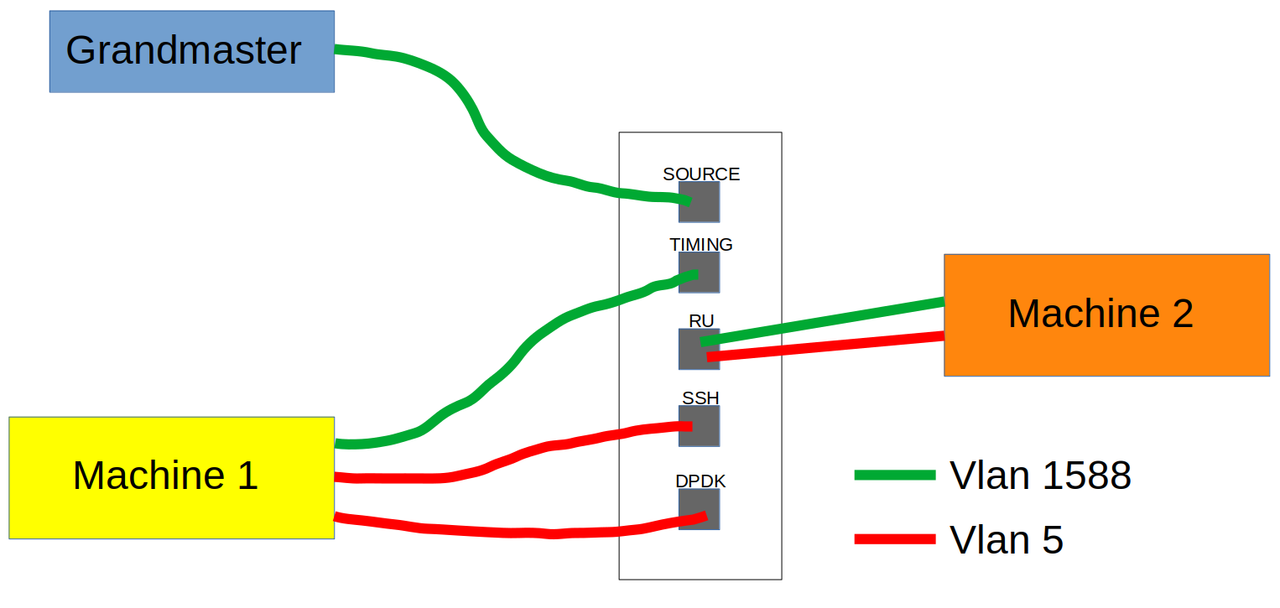
I am working with 5 interfaces:
-SOURCE: ptp sync source from Grandmaster Clock
-TIMING: Port on Machine 1 for ptp sync
-SSH: Port on Machine 1 for ssh connection with Machine 2
-DPDK: Port that sends data to Machine 2
-RU: Machine 2
I would like to use two vlans:
-1588: ptp travels from grandmaster clock to both machine 1 and 2.
-5: packets sent between machine 1 and 2 (must be tagged)
Essentially I want the RU port to be a trunk port to allow both 1588 and 5 vlan traffic simultaneously. The TIMING and SOURCE interfaces can be 1588 access ports and the DPDK and SSH ports can 5 access ports.
I have included my configuration below:
Code: Select all
[admin@MikroTik] > export hide-sensitive
# jan/02/1970 06:01:20 by RouterOS 7.8
# software id = **ELIDED**
#
# model = CRS326-24S+2Q+
# serial number = **ELIDED**
/interface bridge
add admin-mac= **ELIDED** auto-mac=no comment=defconf name=bridge vlan-filtering=yes
/interface ethernet
set [ find default-name=sfp-sfpplus2 ] l2mtu=10218 mtu=10218 name=02-SOURCE
set [ find default-name=sfp-sfpplus9 ] l2mtu=10218 mtu=10218 name=09-TIMING
set [ find default-name=sfp-sfpplus10 ] l2mtu=10218 mtu=10218 name=10-RU
set [ find default-name=sfp-sfpplus11 ] l2mtu=10218 mtu=10218 name=11-DPDK
set [ find default-name=sfp-sfpplus12 ] l2mtu=10218 mtu=10218 name=12-SSH
/interface list
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/port
set 0 name=serial0
/interface bridge port
add bridge=bridge comment=defconf interface=ether1
add bridge=bridge comment=defconf interface=09-TIMING
add bridge=bridge comment=defconf interface=10-RU
add bridge=bridge comment=defconf interface=11-DPDK
add bridge=bridge comment=defconf interface=12-SSH
/interface bridge vlan
add bridge=bridge tagged=10-RU untagged=02-SOURCE,09-TIMING vlan-ids=1588
add bridge=bridge tagged=10-RU untagged=12-SSH,11-DPDK vlan-ids=5
/interface list member
add interface=ether1 list=WAN
add interface=02-SOURCE list=LAN
add interface=09-TIMING list=LAN
add interface=10-RU list=LAN
add interface=11-DPDK list=LAN
add interface=12-SSH list=LAN
/ip address
add address=192.168.20.33/24 comment=defconf interface=sfp-sfpplus1 network=192.168.20.0
/system routerboard settings
set boot-os=router-os enter-setup-on=delete-keyThe Problem:
Using the current configuration, packets are not arriving to the Machine 2 (RU port) from Machine 1 (DPDK) port (and vise-versa). Does anyone know what might be going wrong? I have also tried just setting up all ports as trunk (i.e. not setting DPDK and SSH to access ports but as trunk ports like the RU) and saw the same results.